
As many enterprises move to running AI training or inference on their data, the data and the code need to be protected, especially for large language models (LLMs). Many customers can��t risk placing their data in the cloud because of data sensitivity. Such data may contain personally identifiable information (PII) or company proprietary information, and the trained model has valuable intellectual��
]]>
As more enterprises integrate LLMs into their applications, they face a critical challenge: LLMs can generate plausible but incorrect responses, known as hallucinations. AI guardrails��or safeguarding mechanisms enforced in AI models and applications��are a popular technique to ensure the reliability of AI applications. This post demonstrates how to build safer��
]]>
There is an activity where people provide inputs to generative AI technologies, such as large language models (LLMs), to see if the outputs can be made to deviate from acceptable standards. This use of LLMs began in 2023 and has rapidly evolved to become a common industry practice and a cornerstone of trustworthy AI. How can we standardize and define LLM red teaming?
]]>
AI agents present a significant opportunity for businesses to scale and elevate customer service and support interactions. By automating routine inquiries and enhancing response times, these agents improve efficiency and customer satisfaction, helping organizations stay competitive. However, alongside these benefits, AI agents come with risks. Large language models (LLMs) are vulnerable to��
]]>
As robotics and autonomous vehicles advance, accelerating development of physical AI��which enables autonomous machines to perceive, understand, and perform complex actions in the physical world��has become essential. At the center of these systems are world foundation models (WFMs)��AI models that simulate physical states through physics-aware videos, enabling machines to make accurate decisions and��
]]>
Confidential and self-sovereign AI is a new approach to AI development, training, and inference where the user��s data is decentralized, private, and controlled by the users themselves. This post explores how the capabilities of Confidential Computing (CC) are expanded through decentralization using blockchain technology. The problem being solved is most clearly shown through the use of��
]]>
Training and customizing LLMs for high accuracy is fraught with challenges, primarily due to their dependency on high-quality data. Poor data quality and inadequate volume can significantly reduce model accuracy, making dataset preparation a critical task for AI developers. Datasets frequently contain duplicate documents, personally identifiable information (PII), and formatting issues.
]]>
Federated learning is revolutionizing the development of autonomous vehicles (AVs), particularly in cross-country scenarios where diverse data sources and conditions are crucial. Unlike traditional machine learning methods that require centralized data storage, federated learning enables AVs to collaboratively train algorithms using locally collected data while keeping the data decentralized.
]]>
New research aims to revolutionize video accessibility for blind or low-vision (BLV) viewers with an AI-powered system that gives users the ability to explore content interactively. The innovative system, detailed in a recent paper, addresses significant gaps in conventional audio descriptions (AD), offering an enriched and immersive video viewing experience. ��Although videos have become an��
]]>
As enterprises adopt generative AI applications powered by large language models (LLMs), there is an increasing need to implement guardrails to ensure safety and compliance with principles of trustworthy AI. NVIDIA NeMo Guardrails provides programmable guardrails for ensuring trustworthiness, safety, security, and controlled dialog while protecting against common LLM vulnerabilities.
]]>
As AI models grow in capability and cost of creation, and hold more sensitive or proprietary data, securing them at rest is increasingly important. Organizations are designing policies and tools, often as part of data loss prevention and secure supply chain programs, to protect model weights. While security engineering discussions focus on prevention (How do we prevent X?), detection (Did X��
]]>
General-purpose large language models (LLMs) have proven their usefulness across various fields, offering substantial benefits in applications ranging from text generation to complex problem-solving. However, there are circumstances where developing a bespoke language model becomes not just beneficial but essential. This necessity arises particularly in specialized domains characterized by��
]]>
Edgeless Systems introduced Continuum AI, the first generative AI framework that keeps prompts encrypted at all times with confidential computing by combining confidential VMs with NVIDIA H100 GPUs and secure sandboxing. The launch of this platform underscores a new era in AI deployment, where the benefits of powerful LLMs can be realized without compromising data privacy and security.
]]>
Maritime startup Orca AI is pioneering safety at sea with its AI-powered navigation system, which provides real-time video processing to help crews make data-driven decisions in congested waters and low-visibility conditions. Every year, thousands of massive 100-million-pound vessels, ferrying $14T worth of goods, cross the world��s oceans and waterways, fighting to keep to tight deadlines.
]]>
Synthetic data in medical imaging offers numerous benefits, including the ability to augment datasets with diverse and realistic images where real data is limited. This reduces the costs and labor associated with annotating real images. Synthetic data also provides an ethical alternative to using sensitive patient data, which helps with education and training without compromising patient privacy.
]]>
An easily deployable reference architecture can help developers get to production faster with custom LLM use cases. LangChain Templates are a new way of creating, sharing, maintaining, downloading, and customizing LLM-based agents and chains. The process is straightforward. You create an application project with directories for chains, identify the template you want to work with��
]]>
Imagine an application that can sift through mountains of patient data, intelligently searching and answering questions about diagnoses, health histories, and more. This AI-powered virtual ��clinical assistant�� could streamline preparation for an appointment with a patient, summarize health records, and readily answer queries about an individual patient. Such a system can also be fine-tuned to��
]]>
While harnessing the potential of AI is a priority for many of today��s enterprises, developing and deploying an AI model involves time and effort. Often, challenges must be overcome to move a model into production, especially for mission-critical business operations. According to IDC research, only 18% of enterprises surveyed could put an AI model into production in under a month.
]]>
Following the introduction of ChatGPT, enterprises around the globe are realizing the benefits and capabilities of AI, and are racing to adopt it into their workflows. As this adoption accelerates, it becomes imperative for enterprises not only to keep pace with the rapid advancements in AI, but also address related challenges such as optimization, scalability, and security.
]]>
Prompt injection is a new attack technique specific to large language models (LLMs) that enables attackers to manipulate the output of the LLM. This attack is made more dangerous by the way that LLMs are increasingly being equipped with ��plug-ins�� for better responding to user requests by accessing up-to-date information, performing complex calculations, and calling on external services through��
]]>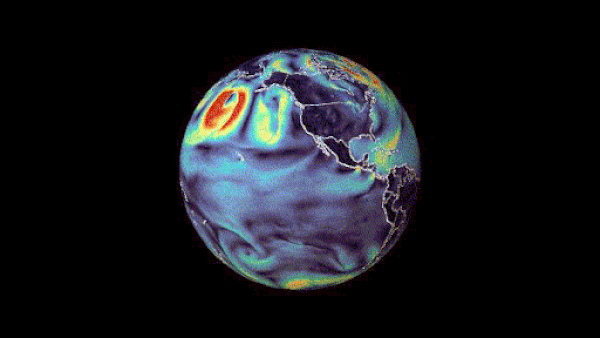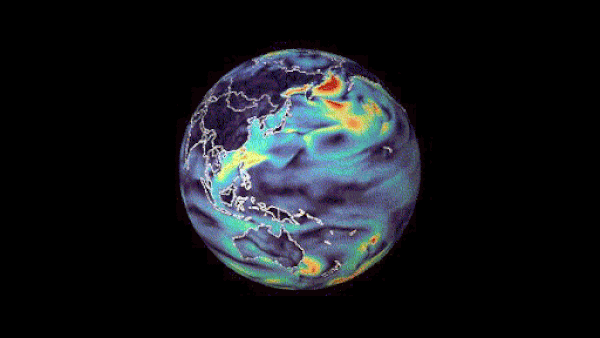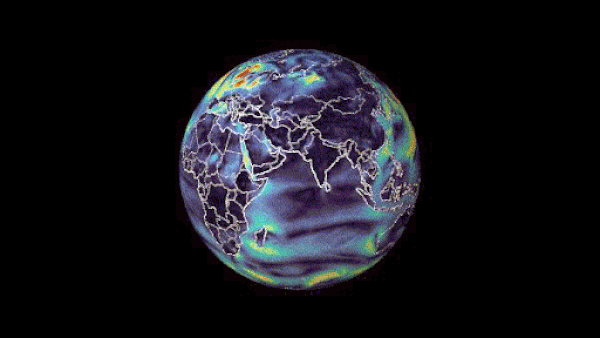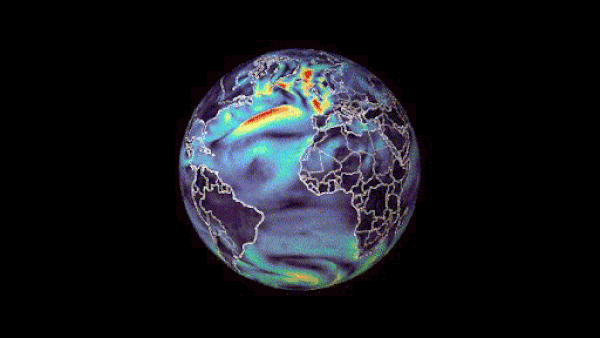
Machine learning-based weather prediction has emerged as a promising complement to traditional numerical weather prediction (NWP) models. Models such as NVIDIA FourCastNet have demonstrated that the computational time for generating weather forecasts can be reduced from hours to mere seconds, a significant improvement to current NWP-based workflows. Traditional methods are formulated from��
]]>
Large language models (LLMs) are incredibly powerful and capable of answering complex questions, performing feats of creative writing, developing, debugging source code, and so much more. You can build incredibly sophisticated LLM applications by connecting them to external tools, for example reading data from a real-time source, or enabling an LLM to decide what action to take given a user��s��
]]>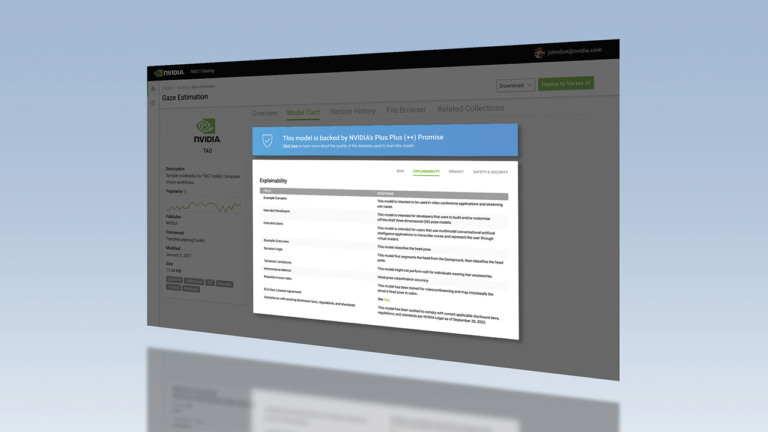
An AI model card is a document that details how machine learning (ML) models work. Model cards provide detailed information about the ML model��s metadata including the datasets that it is based on, performance measures that it was trained on, and the deep learning training methodology itself. This post walks you through the current practice for AI model cards and how NVIDIA is planning to advance��
]]>
On April 21, 2021, the EU Commission of the European Union issued a proposal for a regulation to harmonize the rules governing the design and marketing of AI systems called the Artificial Intelligence Act (AIA). AI systems are considered to be risky by regulatory bodies. High-risk AI systems are subject to specific design and implementation obligations to improve transparency.
]]>