
There is an activity where people provide inputs to generative AI technologies, such as large language models (LLMs), to see if the outputs can be made to deviate from acceptable standards. This use of LLMs began in 2023 and has rapidly evolved to become a common industry practice and a cornerstone of trustworthy AI. How can we standardize and define LLM red teaming?
]]>
Agentic workflows are the next evolution in AI-powered tools. They enable developers to chain multiple AI models together to perform complex activities, enable AI models to use tools to access additional data or automate user actions, and enable AI models to operate autonomously, analyzing and performing complex tasks with a minimum of human involvement or interaction. Because of their power��
]]>
This white paper details our commitment to securing the NVIDIA AI Enterprise software stack. It outlines the processes and measures NVIDIA takes to ensure container security.
]]>
Agentic AI workflows often involve the execution of large language model (LLM)-generated code to perform tasks like creating data visualizations. However, this code should be sanitized and executed in a safe environment to mitigate risks from prompt injection and errors in the returned code. Sanitizing Python with regular expressions and restricted runtimes is insufficient��
]]>
Every day, security operation center (SOC) analysts receive an overwhelming amount of incoming security alerts. To ensure the continued safety of their organization, they are tasked with wading through the incoming noise, triaging out false positives, and sniffing out what could be indicators of a true security breach. However, the sheer quantity of alerts may mean that important early indicators��
]]>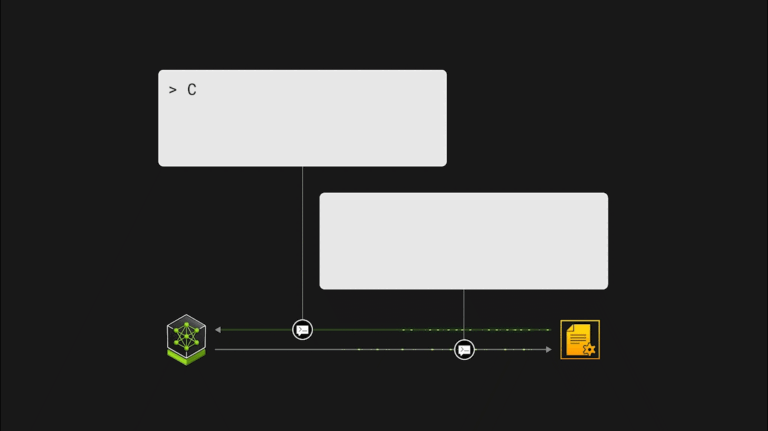
Addressing software security issues is becoming more challenging as the number of vulnerabilities reported in the CVE database continues to grow at an accelerated pace. Assessing a single container for vulnerabilities requires the collection, comprehension, and synthesis of hundreds of pieces of information. With over 200K vulnerabilities reported at the end of 2023, the traditional approach to��
]]>
Modern cyber threats have grown increasingly sophisticated, posing significant risks to federal agencies and critical infrastructure. According to Deloitte, cybersecurity is the top priority for governments and public sectors, highlighting the need to adapt to an increasingly digital world for efficiency and speed. Threat examples include insider threats, supply chain vulnerabilities��
]]>
Each August, tens of thousands of security professionals attend the cutting-edge security conferences Black Hat USA and DEF CON. This year, NVIDIA AI security experts joined these events to share our work and learn from other members of the community. This post provides an overview of these contributions, including a keynote on the rapidly evolving AI landscape��
]]>
As AI models grow in capability and cost of creation, and hold more sensitive or proprietary data, securing them at rest is increasingly important. Organizations are designing policies and tools, often as part of data loss prevention and secure supply chain programs, to protect model weights. While security engineering discussions focus on prevention (How do we prevent X?), detection (Did X��
]]>
This post is part of the NVIDIA AI Red Team��s continuing vulnerability and technique research. Use the concepts presented to responsibly assess and increase the security of your AI development and deployment processes and applications. Large language models (LLMs) don��t operate over strings. Instead, prompts are passed through an often-transparent translator called a tokenizer that creates an��
]]>
Discover how generative AI is powering cybersecurity solutions with enhanced speed, accuracy, and scalability.
]]>
Learn how generative AI can help defend against spear phishing in this January 30 webinar.
]]>
Large language models (LLMs) provide a wide range of powerful enhancements to nearly any application that processes text. And yet they also introduce new risks, including: This post walks through these security vulnerabilities in detail and outlines best practices for designing or evaluating a secure LLM-enabled application. Prompt injection is the most common and well-known��
]]>
At Black Hat USA 2023, NVIDIA hosted a two-day training session that provided security professionals with a realistic environment and methodology to explore the unique risks presented by machine learning (ML) in today��s environments. In this post, the NVIDIA AI Red Team shares what was covered during the training and other opportunities to continue learning about ML security.
]]>
The NVIDIA AI Red Team is focused on scaling secure development practices across the data, science, and AI ecosystems. We participate in open-source security initiatives, release tools, present at industry conferences, host educational competitions, and provide innovative training. Covering 3 years and totaling almost 140GB of source code, the recently released Meta Kaggle for Code dataset is��
]]>
Spear phishing is the largest and most costly form of cyber threat, with an estimated 300,000 reported victims in 2021 representing $44 million in reported losses in the United States alone. Business e-mail compromises led to $2.4 billion in costs in 2021, according to the FBI Internet Crime Report. In the period from June 2016 to December 2021, costs related to phishing and spear phishing totaled��
]]>
Prompt injection is a new attack technique specific to large language models (LLMs) that enables attackers to manipulate the output of the LLM. This attack is made more dangerous by the way that LLMs are increasingly being equipped with ��plug-ins�� for better responding to user requests by accessing up-to-date information, performing complex calculations, and calling on external services through��
]]>
Machine learning has the promise to improve our world, and in many ways it already has. However, research and lived experiences continue to show this technology has risks. Capabilities that used to be restricted to science fiction and academia are increasingly available to the public. The responsible use and development of AI requires categorizing, assessing, and mitigating enumerated risks where��
]]>
Wireless technology has evolved rapidly and the 5G deployments have made good progress around the world. Up until recently, wireless RAN was deployed using closed-box appliance solutions by traditional RAN vendors. This closed-box approach is not scalable, underuses the infrastructure, and does not deliver optimal RAN TCO. It has many shortcomings. We have come to realize that such closed-box��
]]>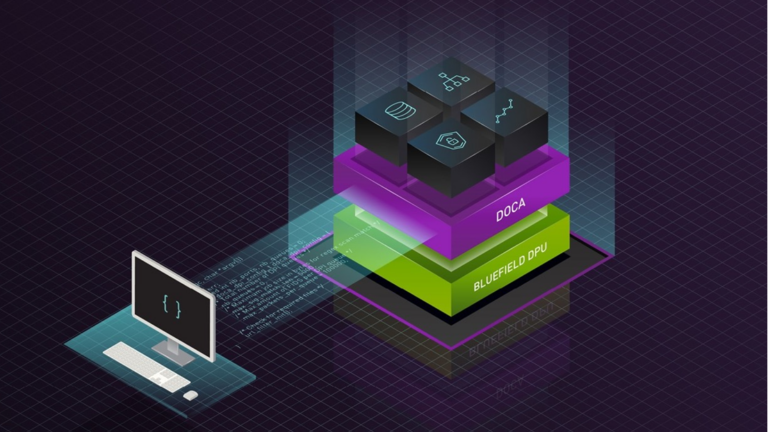
Announced in March 2023, NVIDIA DOCA 2.0, the newest release of the NVIDIA SDK for BlueField DPUs, is now available. Together, NVIDIA DOCA and BlueField DPUs accelerate the development of applications that deliver breakthrough networking, security, and storage performance with a comprehensive, open development platform. NVIDIA DOCA 2.0 includes newly added support for the BlueField-3 Data��
]]>
A shift to modern distributed workloads, along with higher networking speeds, has increased the overhead of infrastructure services. There are fewer CPU cycles available for the applications that power businesses. Deploying data processing units (DPUs) to offload and accelerate these infrastructure services delivers faster performance, lower CPU utilization, and better energy efficiency.
]]>
Deep packet inspection (DPI) is a critical technology for network security that enables the inspection and analysis of data packets as they travel across a network. By examining the content of these packets, DPI can identify potential security threats such as malware, viruses, and malicious traffic, and prevent them from infiltrating the network. However, the implementation of DPI also comes with��
]]>
AI has seamlessly integrated into our lives and changed us in ways we couldn��t even imagine just a few years ago. In the past, the perception of AI was something futuristic and complex. Only giant corporations used AI on their supercomputers with HPC technologies to forecast weather and make breakthrough discoveries in healthcare and science. Today, thanks to GPUs, CPUs, high-speed storage��
]]>
Large language models (LLMs) are incredibly powerful and capable of answering complex questions, performing feats of creative writing, developing, debugging source code, and so much more. You can build incredibly sophisticated LLM applications by connecting them to external tools, for example reading data from a real-time source, or enabling an LLM to decide what action to take given a user��s��
]]>
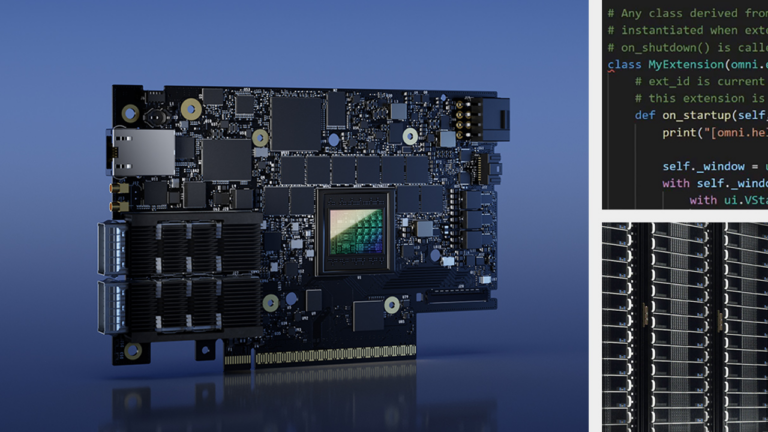
NVIDIA BlueField-3 data processing units (DPUs) are now in full production, and have been selected by Oracle Cloud Infrastructure (OCI) to achieve higher performance, better efficiency, and stronger security, as announced at NVIDIA GTC 2023. As a 400 Gb/s infrastructure compute platform, BlueField-3 enables organizations to deploy and operate data centers at massive scale.
]]>
Using generative AI and the NVIDIA Morpheus cybersecurity AI framework, developers can build solutions that detect spear phishing attempts more effectively and with extremely short training times. In fact, using NVIDIA Morpheus and a generative AI training technique, we were able to detect 90% of targeted spear phishing emails��a 20% improvement compared to a typical phishing detection solution��
]]>
If you asked a group of cybersecurity professionals how they got into the field, you might be surprised by the answers that you receive. With military officers, program managers, technical writers, and IT practitioners, their backgrounds are varied. There is no single path into a cybersecurity career, let alone one that incorporates both cybersecurity and AI. I��ve always been��
]]>
When it comes to new malware written in esoteric programming languages, Blue Team defenders have very little chance to ensure that all endpoints in their organization are able to detect and/or mitigate this malware. Security professionals have quickly recognized this issue and have built an effective pipeline to identify new releases of unique malware and develop detections for them.
]]>
Confidential computing is a way of processing data in a protected zone of a computer��s processor, often inside a remote edge or public cloud server, and proving that no one viewed or altered the work.
]]>
How can you tell if your Jupyter instance is secure? The NVIDIA AI Red Team has developed a JupyterLab extension to automatically assess the security of Jupyter environments. jupysec is a tool that evaluates the user��s environment against almost 100 rules that detect configurations and artifacts that have been identified by the AI Red Team as potential vulnerabilities, attack vectors��
]]>
As part of NVIDIA efforts to advance research towards a more secure data center, the NVIDIA Advanced Development Group is conducting research on quantum key distribution (QKD) technologies, along with other top organizations in Europe and in Israel. The initiatives are funded by the European Union��s Horizon 2020 program and the Israel Innovation Authority. QKD is a highly secure cryptographic��
]]>
Jenkins CI/CD solution provides a way for developers to create an automated, scalable, and highly configurable pipeline to ensure that code bases stay up-to-date and can be pushed out with very little effort. When a developer pushes new commits to any code, Jenkins can pick up on those changes and run a series of tests and builds, then ship it to production in one seamless pipeline.
]]>
The latest NVIDIA Cybersecurity Hackathon brought together 10 teams to create exciting cybersecurity innovations using the NVIDIA Morpheus cybersecurity AI framework, NVIDIA BlueField data processing unit (DPU), and NVIDIA DOCA. The event featured seven onsite Israeli teams and three remote teams from India and the UK. Working around the clock for 24 hours, the teams were challenged with��
]]>
Machine learning (ML) security is a new discipline focused on the security of machine learning systems and the data they are built upon. It exists at the intersection of the information security and data science domains. While the state-of-the-art moves forward, there is no clear onboarding and learning path for securing and testing machine learning systems. How, then��
]]>
Enterprises of all sizes are increasingly leveraging virtualization and hyperconverged infrastructure (HCI). This technology delivers reliable and secure compute resources for operations while reducing data center footprint. HCI clusters rely on robust, feature-rich networking fabrics to deliver on-premises solutions that can seamlessly connect to the cloud. Microsoft Azure Stack HCI is a��
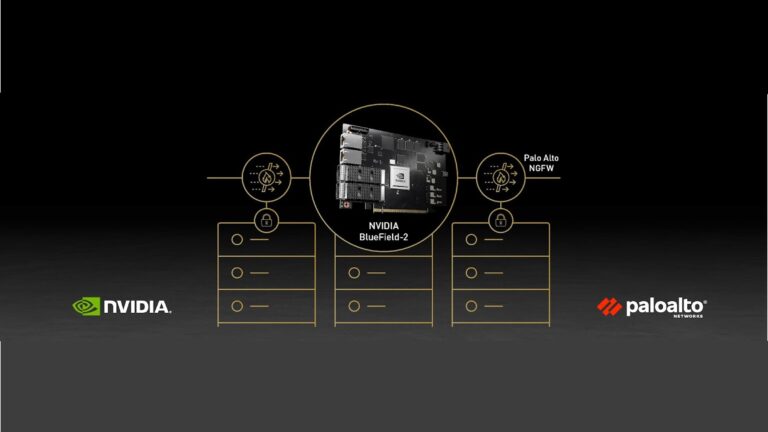
]]>
PTP uses an algorithm and method for synchronizing clocks on various devices across packet-based networks to provide submicrosecond accuracy. NVIDIA Spectrum supports PTP in both one-step and two-step modes and can serve either as a boundary or a transparent clock. Here��s how the switch calculates and synchronizes time in one-step mode when acting as a transparent clock. Later in this post��
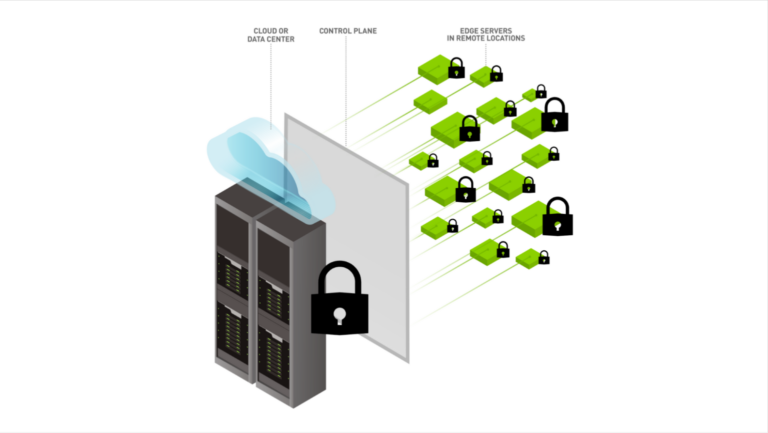
]]>
Cyberattacks are gaining sophistication and are presenting an ever-growing challenge. This challenge is compounded by an increase in remote workforce connections driving growth in secure tunneled traffic at the edge and core, the expansion of traffic encryption mandates for the federal government and healthcare networks, and an increase in video traffic. In addition, an increase in mobile��
]]>
The acceleration of digital transformation within data centers and the associated application proliferation is exposing new attack surfaces to potential security threats. These new attacks typically bypass the well-established perimeter security controls such as traditional and web application firewalls, making detection and remediation of cybersecurity threats more challenging.
]]>
Cybersecurity software is getting more sophisticated these days, thanks to AI and ML capabilities. It��s now possible to automate security measures without direct human intervention. The value in these powerful solutions is real��in stopping breaches, providing highly detailed alerts, and protecting attack surfaces. Still, it pays to be a skeptic. This interview with NVIDIA experts Bartley��
]]>
Today��s cybersecurity landscape is changing in waves with threat and attack methods putting the business world on high alert. Modern attacks continue to gain sophistication, staying one step ahead of traditional cyber defense measures, by continuously altering attack techniques. With the increasing use of AI, ML, 5G, and IoT, network speeds readily run at 100G rates or more.
]]>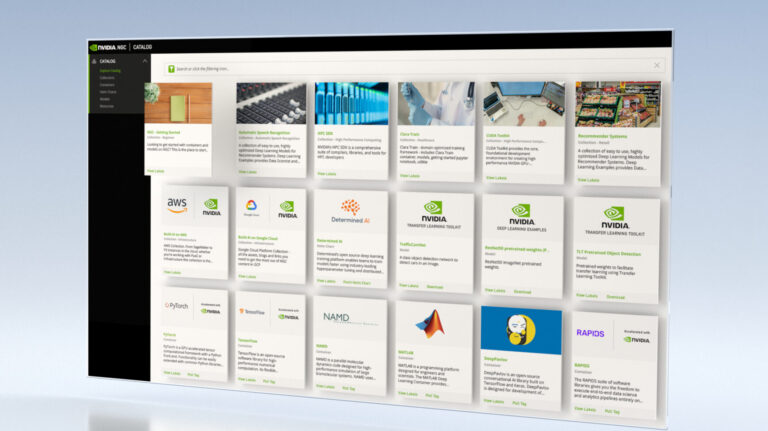
The NVIDIA NGC catalog is a hub for GPU-optimized deep learning, machine learning, and HPC applications. With highly performant software containers, pretrained models, industry-specific SDKs, and Jupyter Notebooks the content helps simplify and accelerate end-to-end workflows. New features, software, and updates to help you streamline your workflow and build your solutions faster on NGC��
]]>
Training resources are always a challenge for IT departments. There is a fine line between letting new team members do more without supervision and keeping the lights on by making sure no mistakes are made in the production environment. Leaning towards the latter method and limiting new team members�� access to production deployments may lead to knowledge gaps. How can new team members learn if��
]]>
AI is transforming the industrial sector. From design, supply chain, and manufacturing, to servicing of mission-critical assets, AI is expected to add $4.8 trillion worth of economic value. The industrial use cases are rich and range from finding anomalies, detecting defects, predicting the health of factory and field assets, to detecting deviations in complex processes monitored by 1000s��
]]>
Today the terms Internet of Things (IoT), 5G, and edge computing are everywhere. With the explosive growth in IoT devices, the emergence of true 5G capable networks, and the growth in AI, organizations are trying to figure out how to use these trends to help them get ahead. As the leader in AI, NVIDIA is bringing these topics to the forefront of our annual NVIDIA GTC, taking place November 8��
]]>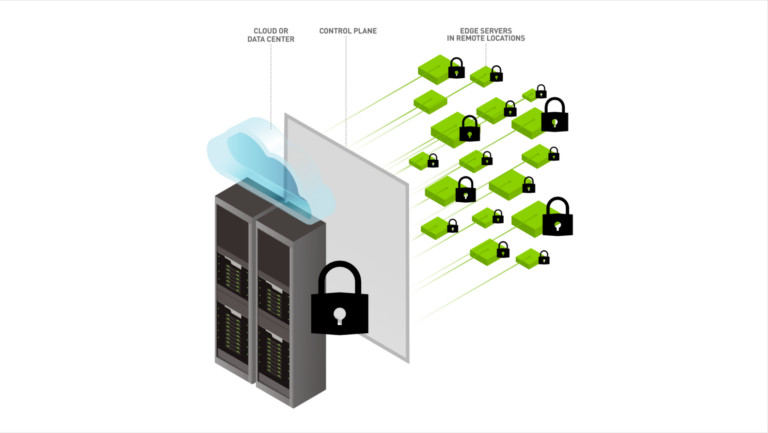
Data is increasingly being generated at remote edge locations out of reach from traditional data center solutions. To take advantage of these sources of data, companies adopt edge computing by moving computing power and storage closer to where the data is collected. This decreases bandwidth costs and latency when streaming data back to a data center or cloud. Edge computing delivers applications��
]]>
Data Processing Units, or DPUs, are the new foundation for a comprehensive and innovative security offering. The hyperscale giants and telecom providers have adopted this strategy for building and securing highly efficient cloud data centers, and it��s now available for enterprise customers. This strategy has revolutionized the approach to minimize risks and enforce security policies inside the��
]]>
The growth of edge computing has been a hot topic in many industries. The value of smart infrastructure can mean improvements to overall operational efficiency, safety, and even the bottom line. However, not all workloads need to be or even should be, deployed at the edge. Enterprises use a combination of edge computing and cloud computing when developing and deploying AI applications.
]]>
Today��s data centers are evolving rapidly and require new types of processors called data processing units (DPUs). The new requirements demand a specific type of DPU architecture, capable of offloading, accelerating, and isolating specific workloads. On August 23 at the Hot Chips 33 conference, NVIDIA silicon architect Idan Burstein discusses changing data center requirements and how they have��
]]>
This post was originally published on the Mellanox blog. In the first post of this series, I argued that it is a function and not a form that distinguishes a SmartNIC from a data processing unit (DPU). I introduced the category of datacenter NICs called SmartNICs, which include both hardware transport and a programmable data path for virtual switch acceleration.
]]>
This is the last installment of the series of articles on the RAPIDS ecosystem. The series explores and discusses various aspects of RAPIDS that allow its users solve ETL (Extract, Transform, Load) problems, build ML (Machine Learning) and DL (Deep Learning) models, explore expansive graphs, process signal and system log, or use SQL language via BlazingSQL to process data.
]]>
DOCA is a software framework for developing applications on BlueField DPUs. By using DOCA, you can offload infrastructure workloads from the host CPU and accelerate them with the BlueField DPU. This enables an infrastructure that is software-defined yet hardware accelerated, maximizing both performance and flexibility in the data center. NVIDIA first introduced DOCA in October 2020.
]]>
NVIDIA recently announced Morpheus, an AI application framework that provides cybersecurity developers with a highly optimized AI pipeline and pre-trained AI capabilities. Morpheus allows developers for the first time to instantaneously inspect all IP network communications through their data center fabric. Attacks are becoming more and more frequent and dangerous despite the advancements in��
]]>
As NVIDIA CEO Jensen Huang stated in last year��s GTC, ��the data center is the new unit of computing.�� Traditional way of using the server as the unit of computing is fading away quickly. More and more applications are moving to data centers that are located at the edge, in different availability zones or in private enterprise clouds. Modern workloads such as AI/ML, edge computing��
]]>Containers have quickly gained strong adoption in the software development and deployment process and has truly enabled us to manage software complexity. It is not surprising that, by a recent Gartner report, more than 70% of global organizations will be running containerized applications in production by 2023. That��s up from less than 20% in 2019. However, containers also bring security��
]]>
Telecommunication (telco) providers are undergoing a business transformation. They��re replacing the traditional network infrastructure that lacks agility, flexibility, and efficiency with commercial off-the-shelf (COTS) white box servers to assist in implementing 5G and modernizing data centers. 5G is the foundation for boosting network capacity and bandwidth but will overwhelm current network��
]]>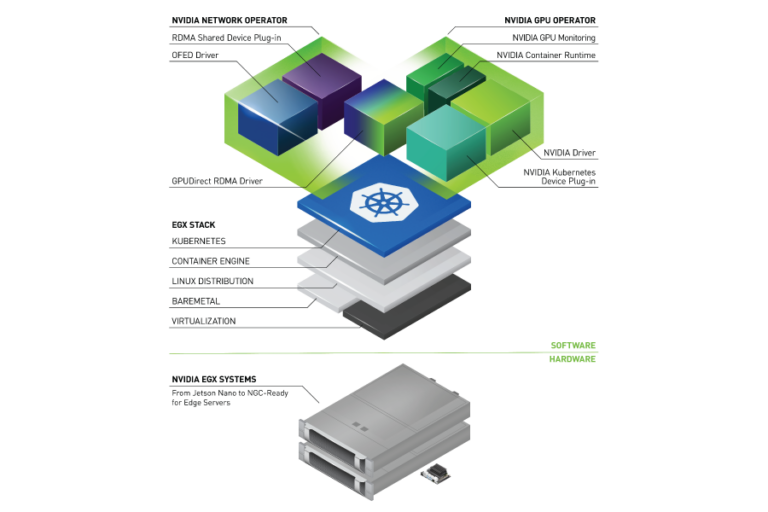
Editor��s note: Interested in GPU Operator? Register for our upcoming webinar on January 20th, ��How to Easily use GPUs with Kubernetes��. Reliably provisioning servers with GPUs can quickly become complex as multiple components must be installed and managed to use GPUs with Kubernetes. The GPU Operator simplifies the initial deployment and management and is based on the Operator Framework.
]]>Public cloud and telecommunication service providers are moving in the direction of large hyperscale datacenters like Google and Amazon. They are looking for ways to increase efficiencies, flexibility, and agility, and so are turning towards disaggregation and server virtualization as critical tenets of their modernization efforts. However, in doing so, they are stumbling across several challenges.
]]>
In an era where cyberthreats are around every corner and with increasing attacks on data centers, security has become an essential element to include in every machine guarding user data. However, many security offerings are defenseless in the presence of malware. Furthermore, software-based security consumes compute and memory resources that should be allocated to users.
]]>