
Missed GTC or want to replay your favorite training labs? Find it on demand with the NVIDIA GTC Training Labs playlist.
]]>
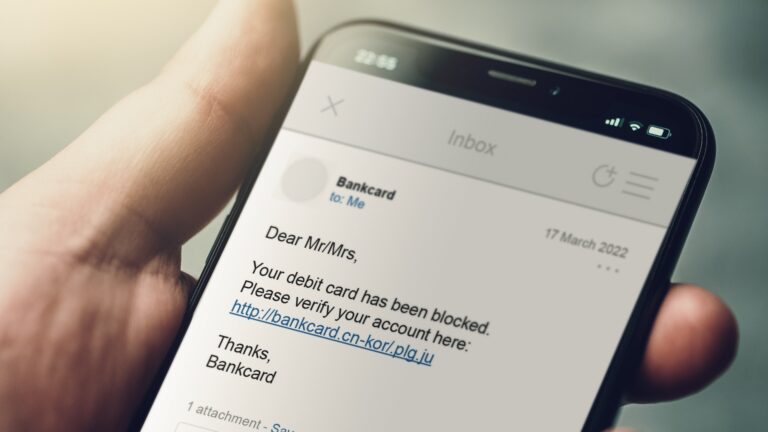
Learn how generative AI can help defend against spear phishing in this January 30 webinar.
]]>
Spear phishing is the largest and most costly form of cyber threat, with an estimated 300,000 reported victims in 2021 representing $44 million in reported losses in the United States alone. Business e-mail compromises led to $2.4 billion in costs in 2021, according to the FBI Internet Crime Report. In the period from June 2016 to December 2021, costs related to phishing and spear phishing totaled��
]]>
Using generative AI and the NVIDIA Morpheus cybersecurity AI framework, developers can build solutions that detect spear phishing attempts more effectively and with extremely short training times. In fact, using NVIDIA Morpheus and a generative AI training technique, we were able to detect 90% of targeted spear phishing emails��a 20% improvement compared to a typical phishing detection solution��
]]>
If you��ve used a chatbot, predictive text to finish a thought in an email, or pressed ��0�� to speak to an operator, you��ve come across natural language processing (NLP). As more enterprises adopt NLP, the sub-field is developing beyond those popular use cases of machine-human communication to machines interpreting both human and non-human language. This creates an exciting opportunity for��
]]>
Use of stolen or compromised credentials remains at the top of the list as the most common cause of a data breach. Because an attacker is using credentials or passwords to compromise an organization��s network, they can bypass traditional security measures designed to keep adversaries out. When they��re inside the network, attackers can move laterally and gain access to sensitive data��
]]>
Network traffic continues to increase, with the number of Internet users across the globe reaching 5 billion in 2022. As the number of users expands, so does the number of connected devices, which is expected to grow into the trillions. The ever-increasing number of connected users and devices leads to an overwhelming amount of data generated across the network. According to IDC��
]]>
Cybersecurity-related risk remains one of the top sources of risk in the enterprise. This has been exacerbated by the global pandemic, which has forced companies to accelerate digitization initiatives to better support a remote workforce. This includes not only the infrastructure to support a distributed workforce but also automation through robotics, data analytics, and new applications.
]]>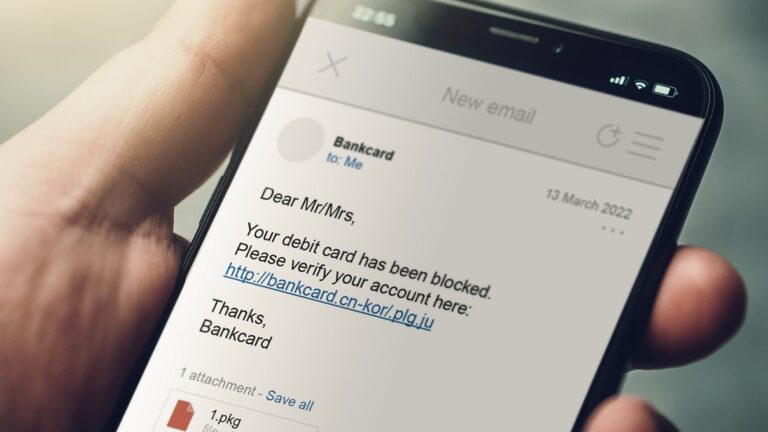
Email became one of the most pervasive, powerful communication tools during the digital revolution. Attempts to defraud users by deceptively posing as legitimate people or institutions through email became so widespread that it got its own name: phishing. Today, with the digital world deeply interwoven in our work and personal lives, phishing remains one of the top three initial infection��
]]>
Cybercrime worldwide is costing as much as the gross domestic product of countries like Mexico or Spain, hitting more than $1 trillion annually. And global trends point to it only getting worse. Data centers face staggering increases in users, data, devices, and apps increasing the threat surface amid ever more sophisticated attack vectors. NVIDIA Morpheus enables cybersecurity��
]]>
Traditional cybersecurity methods include creating barriers around your infrastructure to protect it from intruders with ill intentions. However, as enterprises continue along the path of digital transformation, faced with a proliferation of devices, more sophisticated cybersecurity attacks, and an incredibly vast network of data to protect, new cybersecurity methodologies must be explored.
]]>
This is the last installment of the series of articles on the RAPIDS ecosystem. The series explores and discusses various aspects of RAPIDS that allow its users solve ETL (Extract, Transform, Load) problems, build ML (Machine Learning) and DL (Deep Learning) models, explore expansive graphs, process signal and system log, or use SQL language via BlazingSQL to process data.
]]>
NVIDIA recently announced Morpheus, an AI application framework that provides cybersecurity developers with a highly optimized AI pipeline and pre-trained AI capabilities. Morpheus allows developers for the first time to instantaneously inspect all IP network communications through their data center fabric. Attacks are becoming more and more frequent and dangerous despite the advancements in��
]]>